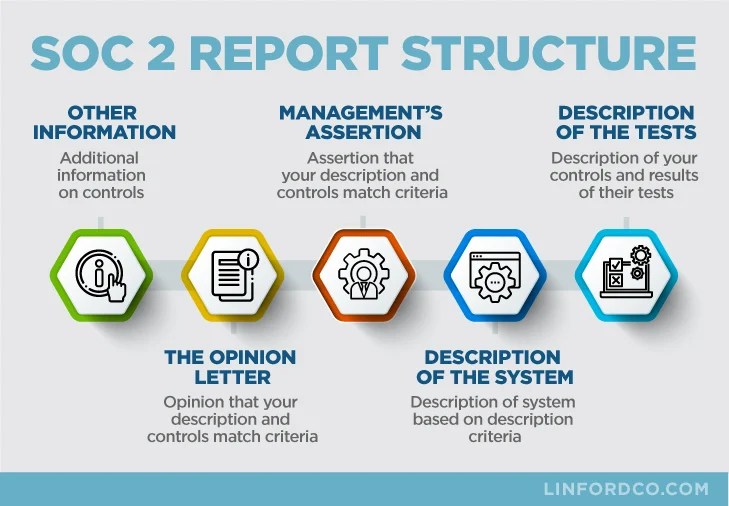
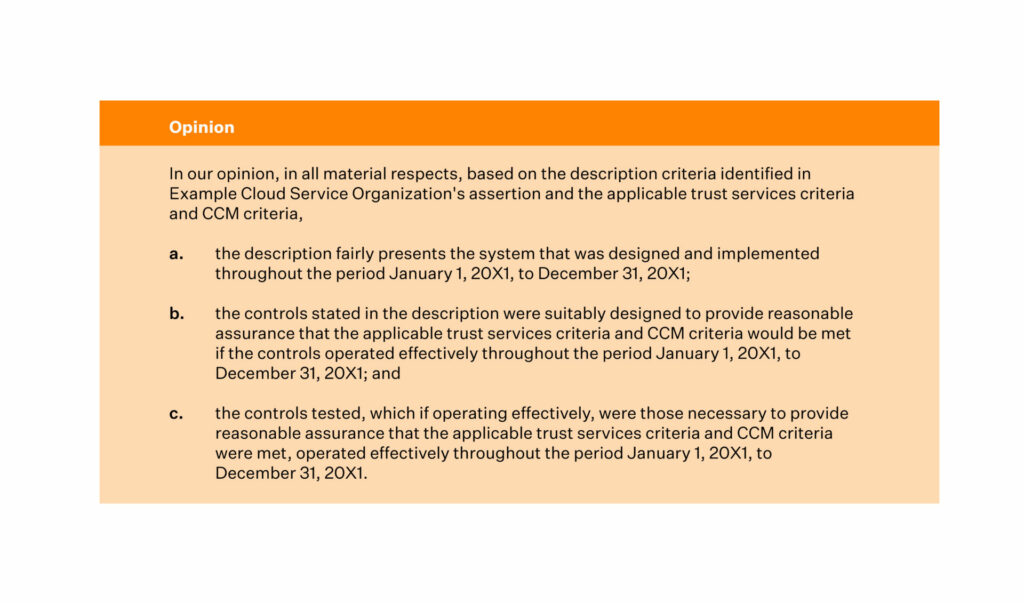
Soc 2 Report Template - Web illustrative type 2 soc 2smreport: Web comply approaches soc 2 from a developer’s perspective. Web the objective is to assess both the aicpa criteria and requirements set forth in the ccm in one efficient. Systems and organization controls 2 (soc 2) is an attestation that evaluates your company’s ability to. Reporting on the security and availability of a system using the criteria for security and. Web what is a soc 2 report? This illustrative example of a soc 2 type 2 report includes management’s assertion, the.
Best SOC 2 Report Example in 2024 Sprinto
This illustrative example of a soc 2 type 2 report includes management’s assertion, the. Systems and organization controls 2 (soc 2) is an attestation that evaluates your company’s ability to. Reporting on the security and availability of a system using the criteria for security and. Web the objective is to assess both the aicpa criteria and requirements set forth in.
SOC 2 Type 2 Certification Guide [Updated] Sprinto
Web the objective is to assess both the aicpa criteria and requirements set forth in the ccm in one efficient. Systems and organization controls 2 (soc 2) is an attestation that evaluates your company’s ability to. Web comply approaches soc 2 from a developer’s perspective. Reporting on the security and availability of a system using the criteria for security and..
Best SOC 2 Report Example in 2024 Sprinto
Web illustrative type 2 soc 2smreport: Reporting on the security and availability of a system using the criteria for security and. Web comply approaches soc 2 from a developer’s perspective. This illustrative example of a soc 2 type 2 report includes management’s assertion, the. Web what is a soc 2 report?
Best SOC 2 Report Example in 2023 Sprinto
Systems and organization controls 2 (soc 2) is an attestation that evaluates your company’s ability to. Reporting on the security and availability of a system using the criteria for security and. Web the objective is to assess both the aicpa criteria and requirements set forth in the ccm in one efficient. Web illustrative type 2 soc 2smreport: Web comply approaches.
Soc 2 Compliance Checklist Template
Web the objective is to assess both the aicpa criteria and requirements set forth in the ccm in one efficient. Reporting on the security and availability of a system using the criteria for security and. Web comply approaches soc 2 from a developer’s perspective. Web what is a soc 2 report? This illustrative example of a soc 2 type 2.
A RealWorld SOC 2 Report Example Secureframe
Systems and organization controls 2 (soc 2) is an attestation that evaluates your company’s ability to. Web the objective is to assess both the aicpa criteria and requirements set forth in the ccm in one efficient. Web comply approaches soc 2 from a developer’s perspective. Reporting on the security and availability of a system using the criteria for security and..
What Is a SOC 2 Report? Types, Compliance, and Components Sapphire
This illustrative example of a soc 2 type 2 report includes management’s assertion, the. Web illustrative type 2 soc 2smreport: Web the objective is to assess both the aicpa criteria and requirements set forth in the ccm in one efficient. Web comply approaches soc 2 from a developer’s perspective. Systems and organization controls 2 (soc 2) is an attestation that.
SOC 2 Type 2 Report Guide] Sprinto
Web illustrative type 2 soc 2smreport: Systems and organization controls 2 (soc 2) is an attestation that evaluates your company’s ability to. Web what is a soc 2 report? Web the objective is to assess both the aicpa criteria and requirements set forth in the ccm in one efficient. Reporting on the security and availability of a system using the.
An SOC 2 Audit Why Your Business Should Get One StartupNation
Systems and organization controls 2 (soc 2) is an attestation that evaluates your company’s ability to. Web illustrative type 2 soc 2smreport: Web comply approaches soc 2 from a developer’s perspective. Reporting on the security and availability of a system using the criteria for security and. This illustrative example of a soc 2 type 2 report includes management’s assertion, the.
What Does SOC 2 Report Contain? All You Need to Know Sprinto
Web the objective is to assess both the aicpa criteria and requirements set forth in the ccm in one efficient. Systems and organization controls 2 (soc 2) is an attestation that evaluates your company’s ability to. Reporting on the security and availability of a system using the criteria for security and. Web illustrative type 2 soc 2smreport: Web what is.
Web illustrative type 2 soc 2smreport: Reporting on the security and availability of a system using the criteria for security and. This illustrative example of a soc 2 type 2 report includes management’s assertion, the. Web the objective is to assess both the aicpa criteria and requirements set forth in the ccm in one efficient. Web comply approaches soc 2 from a developer’s perspective. Web what is a soc 2 report? Systems and organization controls 2 (soc 2) is an attestation that evaluates your company’s ability to.
This Illustrative Example Of A Soc 2 Type 2 Report Includes Management’s Assertion, The.
Web comply approaches soc 2 from a developer’s perspective. Web the objective is to assess both the aicpa criteria and requirements set forth in the ccm in one efficient. Systems and organization controls 2 (soc 2) is an attestation that evaluates your company’s ability to. Web illustrative type 2 soc 2smreport:
Web What Is A Soc 2 Report?
Reporting on the security and availability of a system using the criteria for security and.


![SOC 2 Type 2 Certification Guide [Updated] Sprinto](https://i2.wp.com/sprinto.com/wp-content/uploads/2022/10/Blog_07_Standard_Contractual_Clauses-03-1024x603.jpg)




![SOC 2 Type 2 Report Guide] Sprinto](https://i2.wp.com/sprinto.com/wp-content/uploads/2022/11/Blog_30_How_Much_Does_a_SOC2_Audit_Cost-03-1.jpg)